
WordPress Malware Infections And Ways To Remove It.
Security is a major concern for WordPress users. Cross-site contamination has been used to compromise systems as a result of exploits of vulnerabilities in WordPress' architecture. The extensibility of WordPress makes it more vulnerable; plugins and themes might contain faulty logic, loopholes, Easter eggs, backdoors, and other concerns. When you turn on your computer, you'll notice that you're either supporting a random cause or that you're supporting a specific cause.
The focus of this post is not to add to the overwhelming number of WordPress security or WordPress hardening posts that you see floating around the Web. Rather, we’ll provide more context about the things you need to protect yourself from. What hacks are WordPress users particularly vulnerable to? How do they get in? What do they do to a WordPress website?

What Makes WordPress Vulnerable?
Here’s the simple answer. Old versions of WordPress, along with theme and plugin vulnerabilities, multiplied by the CMS’ popularity, with the end user thrown into the mix, make for a vulnerable website. They do exist; proof can be found in the most recent 5.8.1and 5.8.2 releases. WordPress’ core team has gotten pretty good at rolling out security patches quickly and efficiently, so the risk of exploitation is minimal, provided that WordPress users update their installation. This, unfortunately, is the crux of the problem:
Vulnerabilities in plugins and themes is another issue. The WordPress repository has 20,000 plugins and is growing. The plugins are of varying quality; some of them inevitably have security loopholes, while others are outdated. On top of that, consider all of the themes and plugins outside of the repository, including commercial products that are distributed for free
From My experience , the most common vulnerabilities to website exploits are:
- Out of date software,
- Poor credential management,
- Poor system administration,
- Soup-kitchen servers,
- Lack of Web knowledge,
- Corner-cutting.
Thousands of malware types and infections are active on the Internet; fortunately, not all apply to WordPress. For the rest of this post, we’ll look at four of the most common attacks on WordPress users:
How can I tell whether I’m infected?

Backdoors come in all different sizes. In some cases, a backdoor is as simple as a file name being changed, like this
- wtf.php
- wphap.php
- php5.php
- data.php
- 1.php
- p.php
In other cases, the code is embedded in a seemingly benign file. For instance, this was found in a theme’s index.php file, embedded in legitimate code:
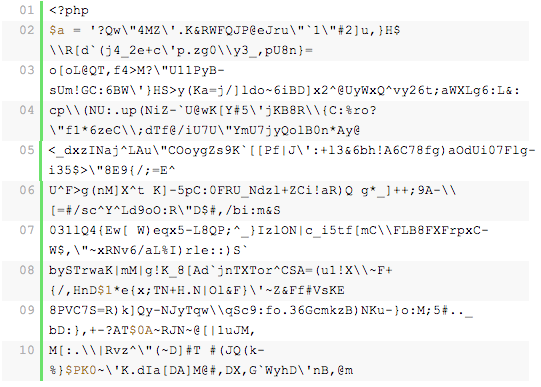
How to fix infected WordPress site
If you choose first approach, you have to follow below steps to fix your site.
Step 1: Backup your site

Before starting the cleanup process, we should take a full backup of our database, and WordPress files because if anything goes wrong or delete any correct file by mistake, we can revert it if we have a backup.
In the previous article, we showed how to backup WordPress Database Manually.
You can also use the backup plugin for taking backup of the site if you can log in at the backend. Sometimes hackers corrupted the database or the host suspends the hosting account. In that situation, you cannot use a backup plugin.
There are many free plugins available for backups like Updraftplus, BackWPup, and Duplicator.
If your database size is large for backup, you can optimize the database before taking backup.
Sometimes the site size is quite larger, over 1 GB. In that case, you should use the manual process for backup: zip all files and take database backup manually.
Step 2: Scan the files and database

After taking backup, we start the cleaning process. First, you should scan all files to know which files are infected.
If you are on VPS, cloud or dedicated server, you can install a scanner like Maldet or ClamAV and scan the entire server via the command line.
Step 3: Clean the files and database
Once the scan is done and has a list of infected files, Our task is to remove infected codes from each file. You can edit your files via Filezilla if you are on FTP or CPanel file editor.
If you have ssh access, you can edit your files with nano command. Sometimes attackers injected the scripts or spammy links at the database, so you should also remove the infection from the database entries. You can connect database via phpmyadmin or adminer.php script.
Step 4: Fix Backdoors

Hackers leave some backdoors to get access to your site again in the future so it is necessary to fix all backdoors. Commonly they use the following PHP functions:
- base64
- eval
- preg_replace (with /e/)
- exec
- str_rot13
- stripslashes
- gzuncompress
- system
- move_uploaded_file
- assert
The following backdoors can be under various folders of the site or plugins and themes folders.
Step 5: Secure the WordPress site

After cleaning all files and database entries, we will follow some necessary steps to secure our site.
Change password and remove unknown administrator
If you have no access to your site backend, you can recover the access by changing the admin password via PHPMyAdmin. If you see any unknown user with administrative privilege, you should remove such type of user and also If you are using default admin username you should remove it and using a custom username
Update plugins and themes
For keeping your site secure, you should keep the site updated. If you see any update available for core, plugins, and themes, you should update immediately. You should also remove all plugins which are not updated by their authors for many years and replace them with a regularly updating plugin.
Install security plugin
Now you should install a security plugin at your site to keep it secure from future attacks.
There are many free and paid plugins available at the repository for setup firewall and regular scanning like Wordfence security Plugin.
If you hire us for malware removal, we will harden your WordPress installation and setup other security fixes manually along with firewall plugin.
Step 6: Tell Google that Our site is Clean and another blacklist removal

Now the time is to remove the site from the blacklist. Google penalizes the infected site and marks the site as infected at search results.
You can submit a request to google by Search Console for removing manual actions and removing warnings from their search results. If you hire us, we will remove your site from all blacklist, including Google, Bing, Macafee, Norton, etc. within 48 Hours.
Conclusions
Prevention is better than cure. Secure your site before hack so keep everything updated and move your site to better and secure hosting!
If you like the post. Do comment, share and follow elitsavvy.

